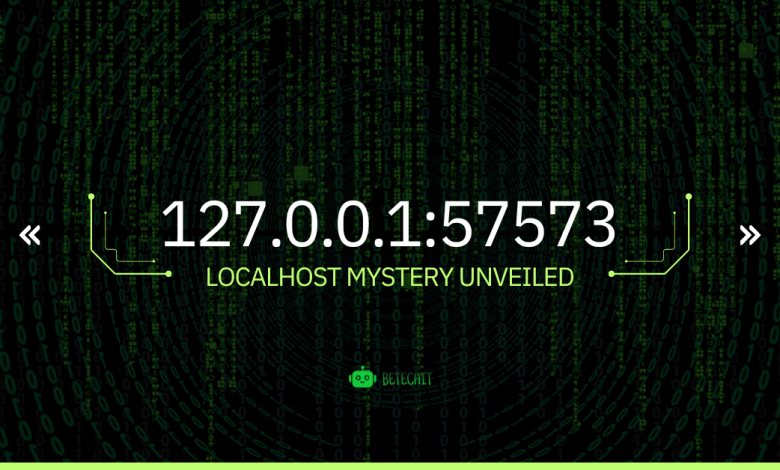
127.0.0.1:57573 — The Heartbeat of Local Networks
Introduction
When it comes to understanding the fundamental workings of computer networking, few phrases are as iconic or as mysterious as “127.0.0.1:57573.” At first glance, this combination of numbers and symbols may appear cryptic to the uninitiated. But to those familiar with the inner workings of the internet and computer systems. It evokes a rich world of network protocols, local environments, development processes, and cybersecurity considerations.
This article will delve into the depths of what “127.0.0.1:57573” represents, exploring both its technical significance and its broader implications for software development, testing, and cybersecurity.
The Anatomy of “127.0.0.1:57573”
To fully understand “127.0.0.1:57573,” we must break it down into its constituent parts. The IP address “127.0.0.1” and the port number “57573.” Together, they form a socket address — a unique identifier for network communication on a computer.
The IP Address: 127.0.0.1
The IP address “127.0.0.1” is universally known as the loopback address. This address is part of the IPv4 address space reserved for loopback purposes. Specifically for testing and development within a single machine. The loopback range covers all addresses from “127.0.0.0” to “127.255.255.255,” with “127.0.0.1” being the most commonly used.
When a network service or application is bound to “127.0.0.1,” it means that the service is only accessible from the same machine. No external device can connect to it, making it a safe environment for testing and development without exposing the service to external networks or potential attackers.
In practice, when you “ping” the address “127.0.0.1,” you’re essentially sending a network packet to yourself. This is useful for testing whether the network stack (the software component of the operating system that manages network communication) is functioning correctly.
The Port Number: 57573
A port number is a 16-bit integer that serves as a communication endpoint for applications running on a device. Port numbers range from 0 to 65535 and are used to differentiate various services running on the same machine. The port number “57573” is within the ephemeral port range (49152–65535), which is often used for temporary or dynamic connections.
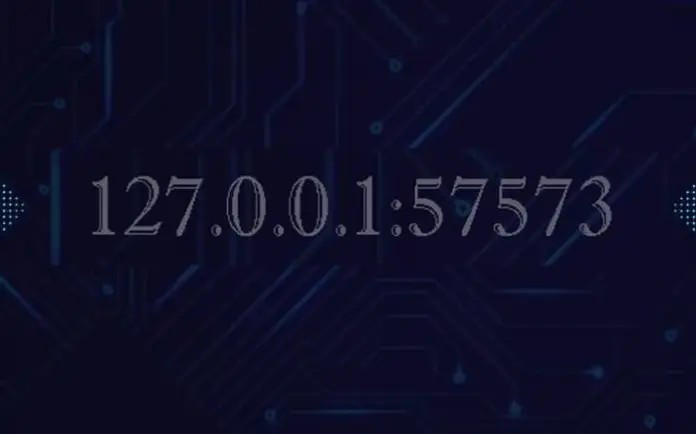
When an application or service runs on a machine and binds to “127.0.0.1:57573,” it indicates that the service is using port number 57573 on the local machine’s loopback interface. This combination allows local applications to communicate with the service while remaining isolated from any external access.
The Technical Significance of “127.0.0.1:57573”
Now that we have a basic understanding of what “127.0.0.1” and “57573” represent, let’s explore their practical applications and significance in more detail.
Local Development and Testing
One of the most common uses of “127.0.0.1:57573” is in local development and testing environments. Developers frequently run services — such as web servers, databases, and application servers — on their local machines during the development process. Binding these services to the loopback address “127.0.0.1” ensures they are only accessible locally. Allowing developers to test functionality without risking exposure to external networks.
For example, a developer might run a web server on “127.0.0.1:57573” to test a web application’s functionality. By binding the server to this address and port, the developer ensures that only their machine can access the application. This isolation is crucial for testing new features, debugging issues, and making changes without affecting the live environment.
Secure Testing Environments
In addition to development, “127.0.0.1:57573” is often used to create secure testing environments. Cybersecurity professionals, for example, might run vulnerable applications on “127.0.0.1” to test exploit payloads. Evaluate security controls, or develop intrusion detection rules. This setup allows them to simulate real-world attack scenarios in a controlled environment without exposing the test environment to the outside world.
Similarly, penetration testers use local addresses like “127.0.0.1” to test the security of applications or services without affecting production systems. By binding a service to “127.0.0.1:57573,” testers can simulate attacks, assess vulnerabilities, and develop mitigation strategies without risking unauthorized access to critical infrastructure.
Local Caching and Proxy Servers
Another common use of “127.0.0.1:57573” is in configuring local caching mechanisms or proxy servers. A proxy server acts as an intermediary between a client and a destination server. Allowing for traffic management, caching, and enhanced security. Running a proxy server on “127.0.0.1:57573” provides full control over the traffic flowing through the local system. Making it an invaluable tool for debugging HTTP requests, optimizing web traffic, or testing caching strategies.
Developers and network administrators often configure applications to use “127.0.0.1:57573” as their proxy server address, allowing them to intercept and analyze traffic in real time. This setup is particularly useful for troubleshooting network issues, debugging application behavior, and ensuring the security of network communications.
Security Considerations of Using “127.0.0.1:57573”
While using “127.0.0.1:57573” for local development, testing, and security assessments offers many advantages. There are also several security considerations that users must be aware of:
- Misconfigured Services: One of the most common security issues arises when services intended to run on “127.0.0.1” are accidentally bound to “0.0.0.0” or a specific external IP address. Unlike “127.0.0.1,” which only allows local access, “0.0.0.0” binds the service to all available network interfaces, potentially exposing it to external networks. This misconfiguration can lead to unintended data exposure, unauthorized access, and other security risks.
- Localhost Bypass Attacks: Some malware and advanced persistent threats (APTs) attempt to bypass local security mechanisms by exploiting services running on “127.0.0.1.” These attacks often involve malicious scripts or binaries that exploit vulnerabilities in locally running services to escalate privileges or execute arbitrary commands.
- Firewall and Access Control Configurations: Firewalls play a critical role in controlling traffic to and from a machine. If a firewall is not properly configured, services running on “127.0.0.1” might inadvertently be exposed to the broader network. Especially in environments where port forwarding, Network Address Translation (NAT), or other network translation mechanisms are in place.
- Denial of Service (DoS) Risks: While services running on “127.0.0.1” are typically isolated from external threats. They are still vulnerable to DoS attacks originating from within the local system. A compromised application running on the same machine could potentially overwhelm other local services, leading to resource exhaustion and service disruption.

Best Practices for Using “127.0.0.1:57573”
To mitigate the risks associated with using “127.0.0.1:57573” in development, testing, and security contexts, it is essential to follow best practices:
- Check and Verify Bind Addresses: Always double-check that services are bound to “127.0.0.1” or “localhost” and not to “0.0.0.0” or any external-facing IP address. Properly specifying the bind address ensures that the service remains isolated to the local machine.
- Implement Strong Authentication and Encryption: Even if a service is running on “127.0.0.1,” it is essential to use strong authentication methods. Such as OAuth, API keys, or tokens, and encryption protocols like SSL/TLS to secure communication. This added layer of security helps prevent unauthorized access and eavesdropping.
- Regularly Update Software and Dependencies: Outdated software, libraries, and dependencies are prime targets for exploitation. Regularly updating software and applying patches helps prevent known vulnerabilities from being exploited.
- Monitor Logs and Network Traffic: Use monitoring tools to keep an eye on logs for any suspicious activity or anomalies. Monitoring both system logs and network traffic can help detect potential breaches or exploits, even in local environments.
- Isolate Services Using Virtual Machines or Containers: Running services in isolated environments. Such as virtual machines or Docker containers, provides an additional layer of security by sandboxing the applications. This isolation helps prevent lateral movement in the event of a compromise.
- Set Up Robust Firewalls and Access Controls: Ensure that firewalls are properly configured to block unwanted traffic and allow only the necessary ports and services. Use access control lists (ACLs) to further restrict access to critical services running on “127.0.0.1.”
Broader Implications for Network Security and Development
The significance of “127.0.0.1:57573” extends beyond just technical configurations. It reflects the essence of how modern software development, testing, and cybersecurity practices are conducted. The ability to isolate services on a local machine, control their exposure, and simulate realistic scenarios is a cornerstone of effective software development and cybersecurity operations.
Moreover, understanding the nuances of network addresses, ports, and their associated security implications is vital for anyone involved in software development, IT, and cybersecurity. As the internet continues to evolve, and with the increasing complexity of software systems, the importance of mastering.